Secure Your Rails Application
The Basics
xdite@rocodev.com

xdite, Rocodev
xdite@rocodev.com



Since Rails 3.0+
(from the beginning)
(from the beginning)
(from the beginning)
(default by 99% Rails auth gem)
(from the beginning)
(default by popular Rails gem)
<%= f.text_field :title %><%= f.text_field :body %>
<input id="topic_title" name="topic[title]" size="30" type="text"><input id="topic_body" name="topic[body]" size="30" type="text">
<input id="topic_title" name="topic[title]" size="30" type="text"><input id="topic_body" name="topic[body]" size="30" type="text"><input id="topic_user_id" name="topic[user_id]" size="30" type="text">
Fake DOM in Chrome Inspector
class TopicsController < ApplicationControllerdef edit@topic = Topic.find(params[:id])if @topic.update_attributes(params[:topic])redirect_to topic_path(@topic)elserender :editendendend
class User < ActiveRecord::Basehas_many :rolesend
role_ids => Getter / Setter<input id="user_title" name="user[title]" size="30" type="text"><input id="user_body" name="user[body]" size="30" type="text"><input id="user_role_ids" name="user[role_ids]" size="30" type="text">
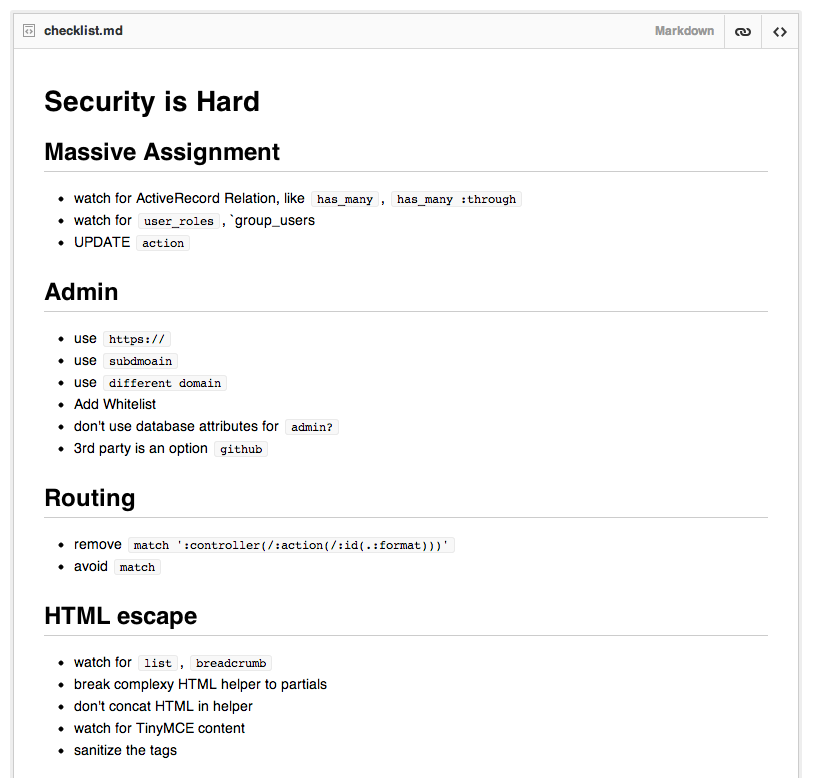
UPDATE actionwhitelist attribute ( remove in Rails 4)Strong parameters (in Rails 4)form object with validations and nested setup of models.def create@form = SongRequestForm.new(song: Song.new, artist: Artist.new)if @form.validate(params[:song_request])....
require 'reform/rails'class UserProfileForm < Reform::Forminclude DSLinclude Reform::Form::ActiveRecordproperty :email, on: :usermodel :uservalidates :email, presence: trueend
/adminadmin.example.orgnethttps://admin.example.orghttps://stop-here.myapp.inwarden-github-rails 3rd party authorationHATE RESTfuldon’t understand RESTfuldon’t think it’s necessary to use RESTful * all the time.# config/routes.rb# This is a legacy wild controller route that's not recommended for RESTful applications.# Note: This route will make all actions in every controller accessible via GET requests.# match ':controller(/:action(/:id(.:format)))'
match ':controller(/:action(/:id(.:format)))'using GET to massive delete articlesnon-RESTful routingmatch is bad smellget, post, put , deletedelete ‘/article/delete/:id’, :to => “articles#destroy” :as => “delete_article”
viamatch ‘/article/delete/:id’, :to => “articles#destroy” :as => “delete_article”, :via => :delete
// SAFEdef render_post_title(post)link_to(post.title, post_path(post))end
list, breadcrumb..etc.// UNSAFEdef render_post_title(post)str = “”str += “<li>”str += link_to(post.title, post_path(post))str += “</li>”return raw(str) // unescape...orzend
raw(str).html_safecategory in list, post title in breadcrumb, user name with glyphicons// SAFEdef render_post_title(post)render :partial => "posts/title_for_helper", :locals => { :title => post.title }end
img, table, tbody, div, span, …def s(html)sanitize( html, :tags => %w(table thead tbody tr td th ol ul li div span fontimg sup sub br hr a pre p h1 h2 h3 h4 h5 h6),:attributes => %w(style src href size color) )end
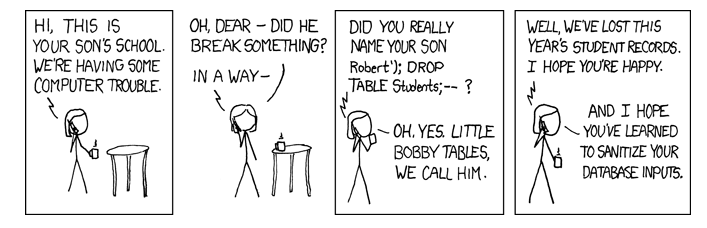
// SAFEUser.where([“name LIKE ?”, params[:q])
// UNSAFEUser.find_by_sql("name LIKE ’%#{params[:q]}%’")
// UNSAFEUser.where(“email = ‘#{params[:email]}’”).first// won’t escape
=> SLELECT “users”.* From “users” WHERE (email = ‘’ OR ‘1’) LIMIT 1
They just don’t know how to use “where” in right ways.
Search Functionsdate, : order, : fieldcomplex joinsfind_by_sql, count_by_sqlransack insteadwhen it's REALLY NESSARYrake secrect to regenerate new key after cloning a Rails new project.google://secret_token.rb site:github.comsecret_token.rb, run rake secrectENV['SECRET_TOKEN'].gitignoreclass TopicsController < ApplicationControllerbefore_filter :login_requiredbefore_filter :check_permission, :only => [:edit]def edit@topic = Post.find(params[:id])endend
class TopicsController < ApplicationControllerbefore_filter :login_requireddef edit@topic = current_user.posts.find(params[:id])endend
EDIT, UPDATE, DESTROY actioncurrent_user.posts ) as 404 Not Foundcancan to authourize resources ( complex permission )3.2.11+